Start with Trezor — Secure Hardware Wallets & Trezor Suite
This page provides a clear, authoritative introduction to initializing and using a Trezor hardware wallet together with Trezor Suite. It outlines the core security model, step-by-step setup considerations, backup standards, device authenticity checks, and ongoing best practices for secure long-term custody.
Overview
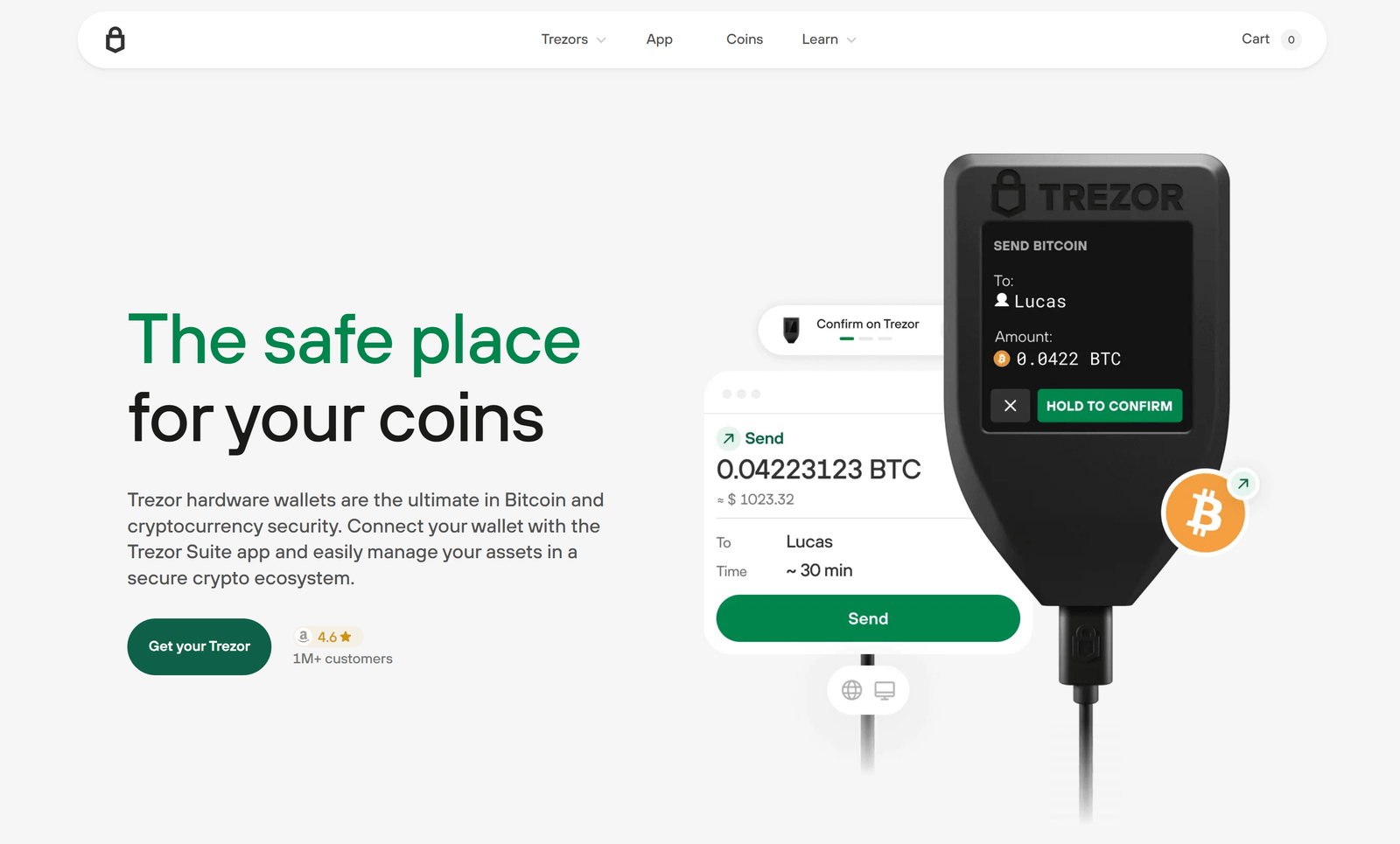
A hardware wallet separates critical cryptographic secrets from internet-connected devices. Trezor devices store private keys inside a secure environment so they are never exposed to the host computer or network during normal use. Trezor Suite is the official companion application for account management, transaction construction and device updates; it acts as a local interface while the device remains the authority for signing. :contentReference[oaicite:0]{index=0}
Core security principles
- Key isolation: Private keys are generated and used on the device only. The host software cannot export these keys.
- Explicit confirmation: All transactions and critical operations must be reviewed and approved on the device screen before signing.
- Offline backups: A wallet backup (formerly called a recovery seed) must be recorded offline and stored in a secure, independent location.
- Authenticity verification: Verify the device and software using official integrity checks before initialising or restoring a wallet.
Set-up overview (informational)
To begin, download Trezor Suite from the official Trezor site or its verified release channel and follow the guided onboarding. Connect your Trezor device, authenticate the device when prompted, and either create a new wallet or restore from an existing wallet backup. The device will display prompts and require physical confirmation for each step — this prevents silent or automated compromises by third-party software. :contentReference[oaicite:1]{index=1}
Wallet backups & recovery
Trezor refers to the recovery mechanism as a “wallet backup.” When a wallet backup is generated, record the backup words exactly and store them offline. Avoid any digital copy (screenshots, cloud storage, phone notes). Trezor provides guides and standards for single-share and multi-share backup strategies for different risk profiles. Only enter wallet backup data when explicitly and directly instructed by the Trezor device during an authenticated recovery flow. :contentReference[oaicite:2]{index=2}
Device authenticity & verification
Before first use, confirm the authenticity of the hardware and the software. Trezor devices include device-level checks and on-device prompts to authenticate firmware and initialization flows. Download Trezor Suite from official sources and, where available, verify checksums or GitHub releases to ensure integrity. If packaging or initialization prompts appear inconsistent, do not proceed and consult official support channels. :contentReference[oaicite:3]{index=3}
Operational best practices
Establish clear operational procedures that reflect your holdings and threat model. For individual users, that typically includes a secure physical copy of the wallet backup, a local device PIN, and a verified Trezor Suite installation. For higher-value or institutional custody, adopt multi-share backups, segregated signing devices, documented approval workflows and periodic audits of access controls. Trezor publishes guidance on personal security standards and threat mitigations to assist deployment decisions. :contentReference[oaicite:4]{index=4}
Maintenance & updates
Keep both device firmware and Trezor Suite updated using official release channels. Updates often include security hardening, new asset support, and UX improvements. Apply updates in a controlled environment and verify release notes via the official site or GitHub repository before installing.
Troubleshooting
Common issues include connectivity interruptions, device recognition problems, or a forgotten PIN. Follow official troubleshooting guides to confirm device firmware, USB/Bluetooth connectivity, and Trezor Suite compatibility. If a device is suspected of compromise, consult official support for recommended remediation steps and avoid entering wallet backup data outside of verified device prompts. :contentReference[oaicite:5]{index=5}
Final guidance
Adopting a hardware wallet is a commitment to self-custody. Combine device hygiene (authentic downloads and firmware updates), robust offline backups, and conservative operational discipline. When used correctly, Trezor devices paired with Trezor Suite create a secure, auditable environment for long-term digital asset stewardship.